Cybersecurity Advisory
Simple, affordable protection. Zero Trust, IAM, compliance, and disaster recovery tailored for SMBs.
Comprehensive Security Solutions
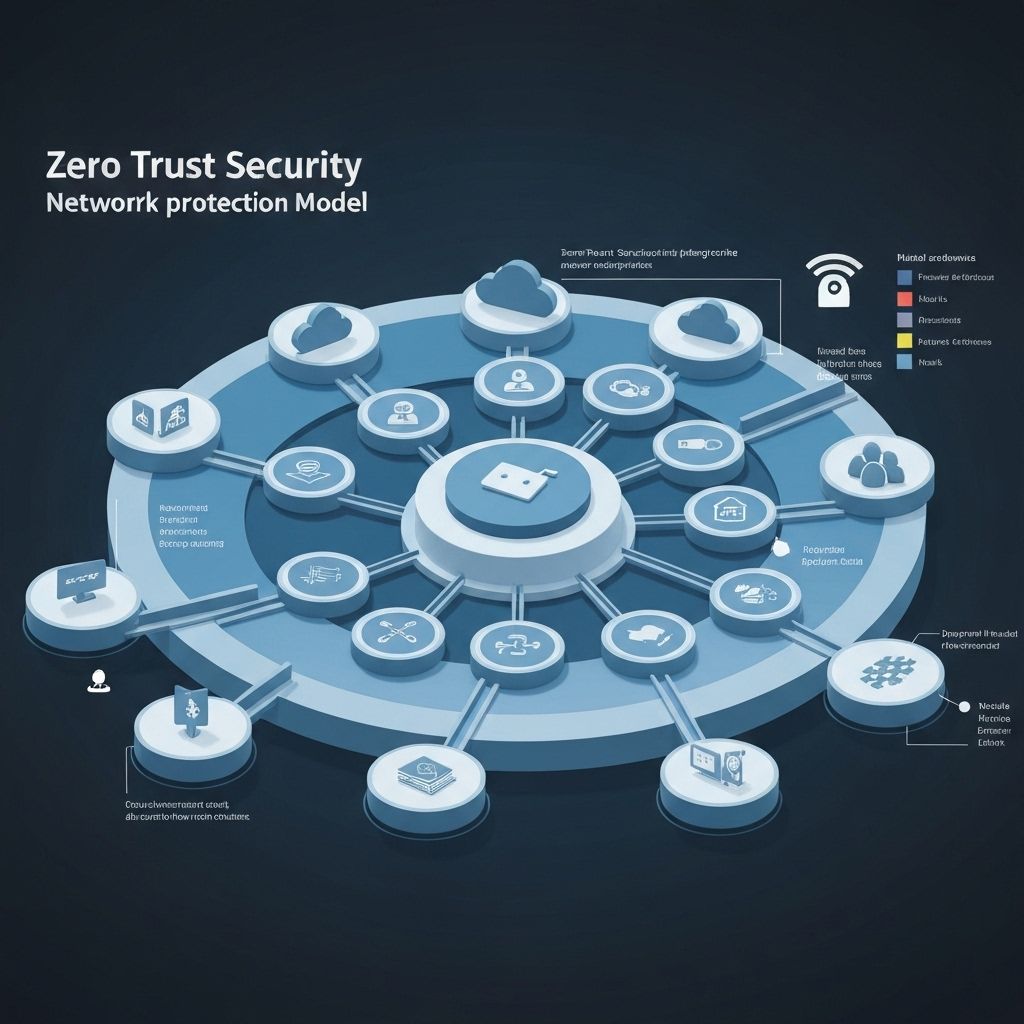
Zero Trust
Implement modern security architecture that never trusts, always verifies with comprehensive identity-based protection.
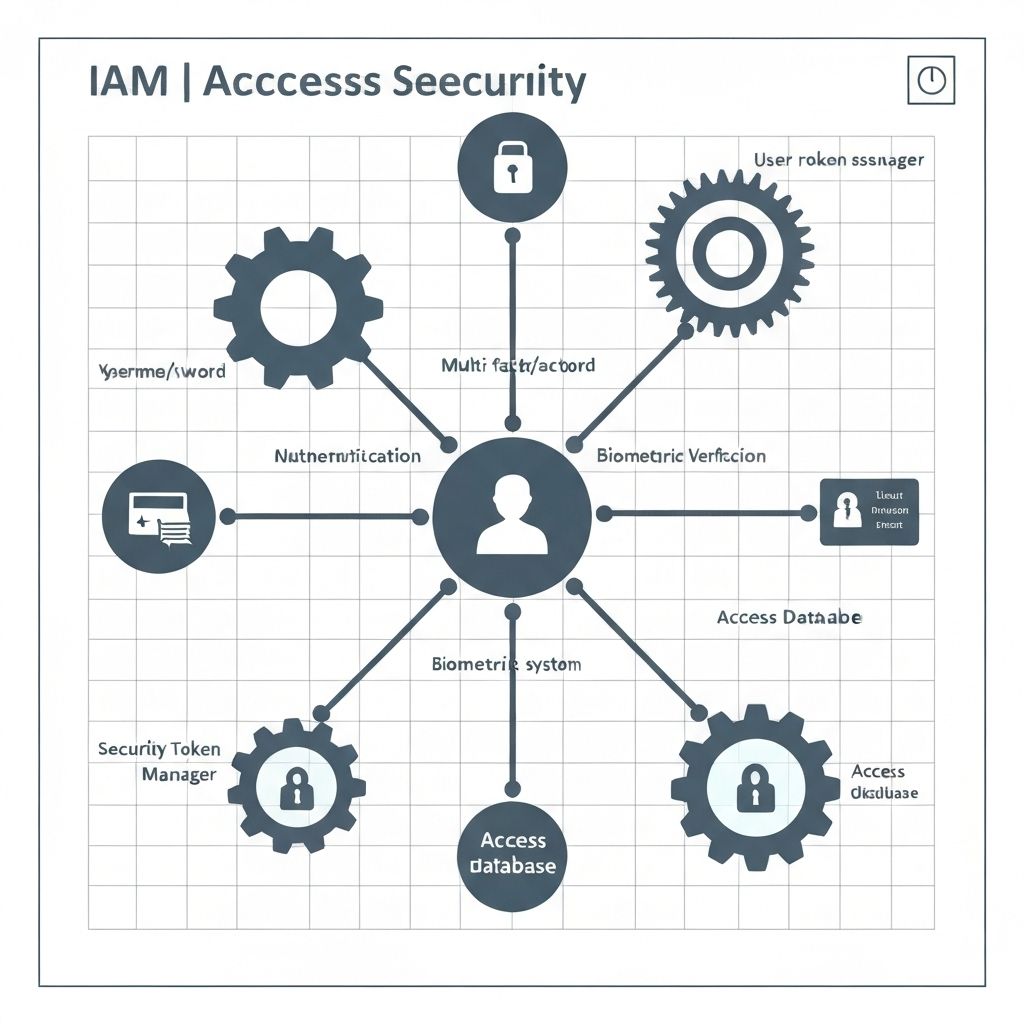
Identity & Access
Secure user authentication and authorization systems with multi-factor authentication and role-based access controls.
Compliance
Meet industry standards and regulatory requirements with confidence through comprehensive compliance frameworks and audit support.

Incident Response
Rapid response and recovery plans to minimize business disruption with 24/7 monitoring and threat detection.
GRC
Establish robust governance, risk, and compliance frameworks to align security practices with business objectives and regulatory requirements.

Privacy Operations
Protect sensitive data and ensure privacy compliance with comprehensive data protection strategies and privacy-by-design principles.

DR BCP
Ensure business resilience with comprehensive disaster recovery and business continuity plans that minimize downtime and protect critical operations.
Our Security Framework
Security Assessment & Gap Analysis
- Comprehensive security posture evaluation across all business systems
- Vulnerability identification and risk assessment with threat modeling
- Prioritized remediation roadmap with budget-conscious solutions
- Cost-effective security improvements with measurable ROI
- Compliance gap analysis for industry-specific requirements
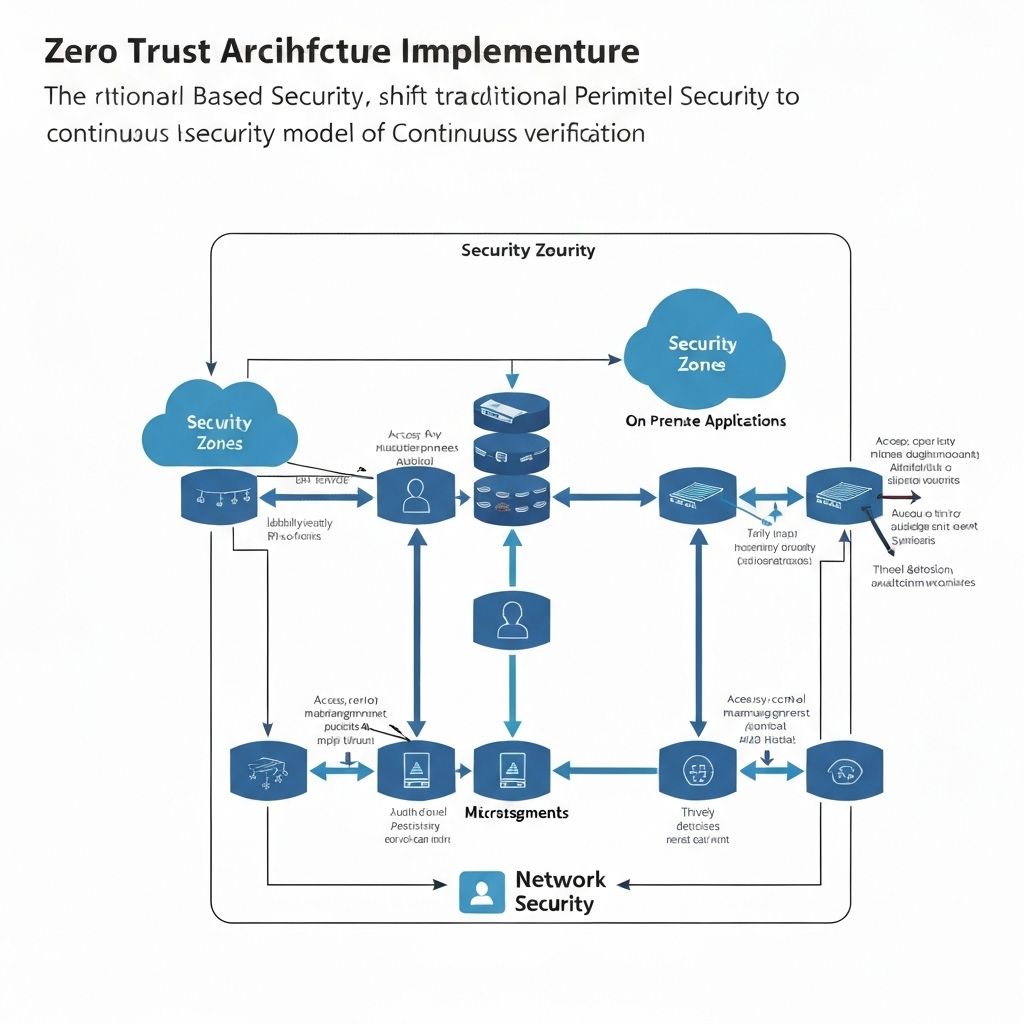
Zero Trust Implementation
- Identity-centric security architecture with comprehensive user verification
- Multi-factor authentication deployment across all business systems
- Network segmentation and micro-segmentation strategies
- Continuous monitoring and verification with real-time threat detection
- Least privilege access controls and dynamic policy enforcement

Disaster Recovery & Business Continuity Planning
- Ensure business resilience with comprehensive disaster recovery and business continuity plans that minimize downtime and protect critical operations.

Privacy Operations
- Protect sensitive data and ensure privacy compliance with comprehensive data protection strategies and privacy-by-design principles.

GRC Framework
- Establish robust governance, risk, and compliance frameworks to align security practices with business objectives and regulatory requirements.
Protect Your Business Today
Don't wait for a security incident. Get affordable, effective cybersecurity protection now.